Also, we recommend you reset your password using a desktop computer with the Google Chrome browser. Please allow a few minutes for the reset email to arrive. Be sure to check your spam email to check for the automated reset email there. We pitted it against the Huawei P20 Pro to find out. Crackutil v1.0 download flexisign pro 10 crack full delta force black. Flexisign pro 10 full activated crack 181.
The modern trend in data security and password access system has become inevitable in the society. Despite the need to secure your files, mark that security issues is like a two sided coin. As far as you may be willing to keep your data more or less confidential and secure, you might forget your password or alter it unknowingly. Here is the solution; Password recovery software for Microsoft Office is available online in addition to the overwhelming number of password crackers today. On the contrary, some of the password crackers aren’t user friendly or extremely insecure. When shopping for office password cracking software, you should weigh between cost and performance. The description given in this section will help you choose between the software qualities that definitely suites your need.
Office password services can crack most Office application files more efficiently and at cheaper cost too. Even more to this, online service offers absolute restoration of access to password protected Office files. The unique technology used to develop the software will help one restore his/her password within no seconds. Apparently, Microsoft built its own variety of password recovery package which addresses the high cost of commercial password crackers. Furthermore, all Passwords of varying character set and length are supported.
Office Password Software
| OFFICE PASSWORD CRACKERS | PRICE | OPERATION SYSTEM |
|---|---|---|
| Free Word password / Excel password recovery software | Free | Microsoft 9x and later Versions |
| Office Password Recovery Lastic | Personal License $59.95 Business $119.85 | Microsoft 97 & Higher versions |
| Office Password Recovery Magic | $47.99 | Microsoft 2000/XP/2003/vista Or higher version of windows |
| Vodusoft Office Password Recovery | Single User $69 or | Microsoft 97/2000/XP & higher version of windows |
| Stellar Phoenix Office Password Recovery | Personal $59.95 Busines $119.85 | Microsoft 2007 & higher versions |
| Office Password Recovery Toolbox | $ 21.55 | Microsoft 97/2000/XP/2003 |
| Office Password Remover | $ 23.95 | Microsoft 97-2010 |
| Office Password Recovery Professional | Basic $60 Standard $120 Profesional $200 Ultimate $350 | Ms Office 97 and higher versions |
| Accent OFFICE Password Recovery | Basic $60 Standard $120 Professional $200 | Microsoft 95 ,97 or higher versions |
| Advanced Office Password Recovery | Home Edition $49 Standard $99 Professional $249 | All versions of Microsoft Office |
1.Free Word / Excel password recovery software
It is free software available for download online developed to counter high software costs. It operates with windows 9X and later PC versions. Recovers passwords for Excel/ Word 97 to Excel/Word 2003 files. Cracks passwords by trying words from a large dictionary on the files and tries several combinations for a match. It cracks the password once it finds the match.
Advantages
- Extremely powerful tool for cracking Excel/ word passwords. Similar free version of the software offers same functionalities as commercial software and effective too.
- Unlike many free software’s, it is completely free and not a shareware or demo version i.e. No cost incurred in use or acquisition.
- In addition, it is free from any malware or spyware.
Disadvantages
- It is likely to take much longer time because it involves testing billions of password combinations.
- It is less effective where the password is complex or extremely long.
2.Office Password Recovery Lastic
- Office Password Recovery Lactic removes or recovers passwords from MS PowerPoint, MS Word, MS Excel, MS Access and MS Outlook documents.
- It is efficient office password software capable of removing multiple passwords from a number of office files at once. Enables revealing of lost VBA password too.
- Multi-language support is enabled with friendly user interface. Password recovery is quite simple even for first time users.
- Supports Microsoft Office XP/97/2000 to 2007.
- It provides protection for a range of document types; document protection passwords, passwords to modify, worksheet and workbook passwords (Only Excel), user workgroup (only Access) and database.
Advantages
- Regardless of the complexity of the password, the software takes only a few second to crack a password.
- Confidential information is strictly guarded against unauthorized access.
- The original document is not modified. The program works with a copy of the document without changing the original copy.
Disadvantages
- The software is available at a cost. The cost incurred may be relatively expensive and restricted to a given user.
3.Office Password Recovery Magic
The software is used to recover either forgotten or lost password. It mainly applies for recovering read only password protected files. The range of application files includes; .doc, .ppt, .xls, .mdb and Office 2007 file formats.
The user interface is designed to help with exact search. Users are able to set parameters to exact range of password they need to search i.e. shape and length of password. Alternatively, users can use dictionary for a quicker password match.
Advantages
- Recover lost or forgotten password more quickly.
- Recovers read-only passwords for MS Excel, word, PowerPoint and Access.
- User-friendly interface.
- Installation is easy
- Dynamic; user have a variety of option to choose from while recovering their password.
Disadvantages
- It is relatively expensive to acquire or access because it is commercial software.
- It only works for Microsoft Windows 2000/XP/2003/vista and higher version but not older versions like Windows 95/98.
4.Vodusoft Office Password Recovery
The software is designed specifically for the recovery of forgotten/lost password for MS PowerPoint, Access, Outlook, Excel and Word. The software renders three type of attack: Dictionary Attack, Brute Force Attack with Mask Attack and Brute-Force Attack. It is highly optimized to recover extremely complex password with high speed performance.
Apparently, it supports document type: MS Outlook (*.pst), Word (*.doc,*. docks), Access (*.mdb,*.accdb), PowerPoint (*.ppt,*. pptx) and Excel (*.xls,*.xlsx)
Advantages
- Highly optimized to reduce time for cracking password.
- Supports ATI (Advanced Technology Interface) video cards hardware acceleration.
- User-friendly interface with minimum understanding requirement.
- The software performs read-only operation on user document when recovering a password. This cautions against damage to any office document.
- Recovery results are automatically saved for next use.
- The program supports auto shutdown function once the password is recovered.
- Updates are free for new versions released.
Disadvantages
- Trial version of the software only supports up to 4 character password cracking.
5.Stellar Phoenix Office Password Recovery
Features
The program is more efficient and quick for recovering passwords set to MS Office files with either open or modify property.
It works with most version of MS Office.
Its additional features enable one to specify the possible range of the password length.
The software cracks the password by generically tying out a combination of characters of the given length.
While the software performs the recovery, it shows the process status such as expected completion time and speed.
Advantages
- Recovering -‘Password to Modify or ‘Password to open ‘for MS Office files.
- Employs the Brute-Force attack to recover passwords more accurately.
- Facilitates masking of the process to minimize recovery time
- The program is optimized to maintain dynamic dictionary that contains all recovered passwords.
- The tool offers users a variety of choices for easier recovery or cracking of complex passwords within no time.
- The program generates a log off report of the entire password recovery process that can be stored in a file for reference.
Disadvantages
- The software might not work best for all cases of password lengths.
6.Office Password Recovery Toolbox
The office password recovery tool supports MS Access, Word, Outlook, Excel, PowerPoint and VBA projects. Its features like the quick search allows for recovery of recently opened Office document. Using the software tool is easy due to the superb interface developed for users. Cracking a password virtually takes a few seconds too. It work well for Office 97/ XP /2000 /2003/2007/2010.
Advantages
- Provides an instant recovery or removal of passwords ranging from MS PowerPoint, VBA projects, Access, Word, Outlook ,Excel, workgroup passwords(only Access),worksheet & workbook passwords(only Excel) to database passwords.
- Supports multi-lingual interface and superbly simple to use.
- Quickly removes recently opened Office document upon start up.
- The program accesses a unique server that can break MS Excel and MS Word protected document regardless of strength or length.
- Highly secure for recovering information within the document.
Disadvantages
- It is not effective for some documents versions that do not allow removal or recovery of certain types of passwords.
7.Office Password Remover
The software is one of the fastest when it comes to password recovery or removal. It can remove or unlock both Excel and Word documents in seconds. It either applies the Brute-Force technique or uses the Office Password Remover to remove the password directly. The software supports MS Word 97 to2010 (.doc) and MS Excel 97 to 2010(.xls).It is Compatible with Windows 8/7/Vista/XP, Windows server 2008/2003/2000 x32bit or x64bit.
Advantages
- 100% recovery rate for lost MS Word/Excel passwords.
- Supports MS Word/Excel 97-2010 and the associated file types i.e. Excel (*.xls) and Word (*.doc).
- The software is highly optimized for multiprocessor systems for great recovery speeds.
- The user interface is simpler and customized for novice users
- Additional online services is offered with maximum security and privacy guaranteed.
- It is not limited by the password length or complexity
- The program is optimized to support multiple languages.
Disadvantages
- Trial version of this software only test MS Word/Excel document protected with “open property” but cannot open it if still protected.
8.Office Password Recovery Professional
Office Password Recovery Professional provides valid solution to Microsoft Office programs. Office Password Recovery works with all versions of MS Office. It automatically obtains all editing and formatting restrictions, shared protection password and locked cells.
Advantages
- Recovers passwords almost instantly regardless of length or complexity.
- Offers multilingual support and can recover Cyrillic characters, Latin and hieroglyphics.
- Highly capable of combining two types of attack (Brute Search, Smart search and dictionary-based) or applying them one by one.
- The software woks instantly for weak office passwords.
- It processes several files simultaneously with enhanced password recovery speed.
- Highly customized functionality with program priority mode and option for providing password information.
- Password can be recovered by just a button click because of its easy interface.
- The Auto Save feature is very convenient for users.
- Professional support and free update for up to 12 months.
Disadvantages
- Trial version of the software does not provide all the functionalities.
9.Accent OFFICE Password Recover.
Features
- The software the software available in a number of varieties .It supports all file formats generated with Open Office or MS Office ranging from any year.
- Works for windows 7/8 and earlier versions.
- The program works majorly in three ways; dictionary, brute-force or mask attacks.
- The software automatically recovers passwords with additional functionality for user-defined or predefined parameters.
- Mutation rules can be added to the dictionary by included macro language functionality.
Advantages
- Supports Ms Office 2000 to 2013 and OpenOffice 1-4
- NVIDIA and AMD graphic cards enable to search 40 times faster.
- Efficient speeds for all Intel and AMD processors.
- The program offer best performance relative to its price.
- Guarantees’ ultimate access and decryption of Word and Excel 97/2000 files.
- It has additional GPU technology that is capable of recovering the toughest password encryptions
Disadvantages
- Trial versions only display the first two symbols of the password, does not save recovery status file and runs for longer time.
10.Advanced Office Password Recovery
Features
Advanced Office Password Recovery replaces, recovers and removes passwords from protected MS Office documents almost instantly. It supports all versions of Microsoft office. The software unlocks documents in Hangul Office and Open Document formats. In addition to these, it recovers Access, Excel, Outlook, Project, PowerPoint, Visio, Money, Publisher, Word and OneNote passwords. It exploits the backdoor technique to unlock any protected VBA project and reset MS internet Explorer contents.
Advantages
- It supports Hangul Office documents
- The software instantly recovers passwords for multiple products.
- Unlock documents with previously recovered password instantly.
- It explores all the known tricks and backdoors in the Office family for an instant recovery.
- Additional hardware acceleration capabilities reduces password recovery period by a factor of 50.
- The software is highly optimized with a low-level code to increase performance.
- The program is designed to utilize CPU time more efficiently.
Disadvantages
- With the rise of new versions like MS Office 2013, recovering from the strongest security become painfully slow and inefficient even with the aid of GPU accelerated environments.
VBA PASSWORD RECOVERY TOOL
| Password Recovery Tool | URL | Price | Operation System |
|---|---|---|---|
| Excel Tool VBA Password Recovery | http://www.excel-tool.com | $29.95 | Microsoft Excel 97/2000/XP/2003/2007 or higher. |
| VBA Password Recovery Master | http://www.rixler.com | Personal $29.95 Bussines $59.85 | MS Word, MS Excel, MS Outlook 97/2000/XP/2003/2007/2010, MSPowerPoint 2007/2010. |
| VBA Password | http://lastbit.com/register.asp | $39 | Microsoft Office 97 to 2007 |
| Advanced VBA Password Recovery | http://www.openwall.com/cgi/redirect.cgi?elcomsoft-vba | $79 Professional $199 | Microsoft Office 97 to 2007 |
| Reset VBA Password | http://store.esellerate.net/s.aspx?s=STR2648995036 | $29.00 | Microsoft Office 2007-2013 |
1.Excel Tool VBA Password Recovery
The software application is designed to recover vba protected projects file with extensions like (.xls, .xlam). It recovers both forgotten and lost password. The application supports recovery of passwords of any length or complexity.VBA applications are supported with additional recovery for MS Excel 97 to 2010 file formats passwords. Its design and application can easily recover or open VBA projects with protected passwords.
Features:
Price: Freeware
Software requirements: Ms Excel 97/XP/2000 to 2007 or higher.
Current Version: 10.6.1
File Size: 0.5(MB)
Platform: Windows2000/7/XP/Vista
Advantages
- It is applicable for all password lengths and complexities.
- Use computer resources more efficiently.
- Applicable for most Microsoft Excel versions
- The software is available as a Freeware.
- Easy user interface with additional functionality buttons.
- The software is easy to acquire and distribute.
Disadvantages
- It is relatively slow when recovering complex or lengthy passwords.
- It is only applicable to a few MS Excel file formats.
2.VBA Password Recovery Master
VBA Password Recovery Master software does exactly the recovery of password for Microsoft Office documents. It supports MS Excel, Word, PowerPoint and Outlook. The software displays the password on the screen immediately it cracks it. It automatically searches for protected documents within Office files and generates the password instantly.
Advantages
- It cracks VBA projects passwords in Outlook, PowerPoint, Excel and Word documents instantly.
- The program support all the major versions of Microsoft Office tools i.e. Outlook, PowerPoint, Excel and Word documents (97/2000/XP/2003/2007/2010 versions).
- The auto-search function enables users to locate all VBA projects and Microsoft Office documents with passwords and recovers their passwords.
- Provides 100% reliable password recovery or removal for VBA projects.
- The restored password is copied to the clipboard for your view.
- It is designed to restore lost passwords for VBA with minimum effort.
- It is absolutely safe.
Disadvantages
- The software does not fully support Microsoft Office 2013 versions.
3.VBA Password
VBA Password software recovers your data to the very last bit. It can recover password for VBA project in different modules (Excel and Word documents, Access,databases). Additionally, it supports universal VBA password recovery applicable for all VBA applications.
Features
VBA works with two fundamental recovery engines: the first is designed for MS Access, Excel and Word files. It supports Access XP/2003 and all versions of Excel.
The second method employs a universal recovery technique that facilitates the recovery of VBA modules in any application. Brute-force attack is used to recover passwords for Office 2000/XP documents.
Advantages
- Genuine version of VBA recovery tool is capable of recovering all passwords in Office documents right from Ms Office 97.
- If the cracking takes longer, an alternative way can be followed by resetting the password to a known one.
- It provides instant access to password-protected VBA project.
- The software provides an additional universal recovery method that enables recovery of VBA project in any application
Disadvantages
- It occasionally takes much longer to recover more complex or longer passwords.
4.Reset VBA Password
Features
Reset VBA Password is a software utility for cracking password protected VBA project Modules in Microsoft Office documents (Word, Excel, Project and Power Point). It is widely applied in Office documents and other applications that use VBA macros. The program makes office a better environment by automating most office task.All legal versions of Ms Office from 97, XP, 2003 to 2007 is supported.
Advantages
- It supports the latest versions of Ms Office (2007 to 2013) and all legal versions of 97, 2000, XP and 2003.
- The software recovers all type of passwords (multi-lingual passwords included).
- The program supports command line for running the application in batch mode.
- It removes password securely without damage to personal files or documents and automatic backups.
Disadvantages
- It does not support Ms Access and Outlook file formats
5.Advanced VBA Password Recovery
The software is available as a commercial-off the shelf software by ElcomSoft. The program cracks lost or forgotten passwords for Visual Basic for Applications (VBA) in edit or view mode. The software supports Ms Outlook, Access, Word, Project, Excel, Visio and PowerPoint documents. It has additional capabilities of unlocking protected Excel add-ins. Luckily; it works with other VBA enabled applications such as WordPerfect Office, Corel and AutoCAD. All versions of Ms Office (97 to 2007) are supported-either by backdoor or directly.
Advantages
- Resolves all password protected VBA files more efficiently.
- It supports additional functions for unlocking Excel add-ins.
- The software recovers VBA passwords more instantly.
- It recovers password for VBA source code
- The VBA Password Recovery software supports most versions of Microsoft Office document file formats.
Disadvantages
- The software does not perfectly work for latest version for Microsoft Office (Ms Office 2013).
- It becomes extremely slow when the password length is longer or more complex.
Hackers use a variety of means to gain passwords. One of the most common ways for hackers to get access to your passwords is through social engineering, but they don’t stop there. Check out the following tools and vulnerabilities hack exploit to grab your password.
Keystroke logging
One of the best techniques for capturing passwords is remote keystroke logging — the use of software or hardware to record keystrokes as they’re typed.
Be careful with keystroke logging. Even with good intentions, monitoring employees raises various legal issues if it’s not done correctly. Discuss with your legal counsel what you’ll be doing, ask for her guidance, and get approval from upper management.
Logging tools used by hackers
With keystroke-logging tools, you can assess the log files of your application to see what passwords people are using:
- Keystroke-logging applications can be installed on the monitored computer. Check out Spector 360 by SpectorSoft. Dozens of such tools are available on the Internet.
- Hardware-based tools, such as KeyGhost, fit between the keyboard and the computer or replace the keyboard.
- A keystroke-logging tool installed on a shared computer can capture the passwords of every user who logs in.
Windows 10 Password Crack Tool
Countermeasures against logging tools
The best defense against the installation of keystroke-logging software on your systems is to use an antimalware program or a similar endpoint protection software that monitors the local host. It’s not foolproof but can help. As with physical keyloggers, you’ll need to inspect each system visually.
The potential for hackers to install keystroke-logging software is another reason to ensure that your users aren’t downloading and installing random shareware or opening attachments in unsolicited emails. Consider locking down your desktops by setting the appropriate user rights through local or group security policy in Windows.
Alternatively, you could use a commercial lockdown program, such as Fortres 101 for Windows or Deep Freeze Enterprise for Windows, Linux, and macOS X. A different technology that still falls into this category is Carbon Black’s “positive security” allowlisting application, called Cb Protection, which allows you to configure which executables can be run on any given system. It’s intended to fight off advanced malware but could certainly be used in this situation.
Weak password storage
Many legacy and stand-alone applications — such as email, dial-up network connections, and accounting software — store passwords locally, which makes them vulnerable to password hacking. By performing a basic text search, you can find passwords stored in clear text on the local hard drives of machines. You can automate the process even further by using a program called FileLocator Pro.

How hackers search for passwords
You can try using your favorite text-searching utility — such as the Windows search function, findstr, or grep — to search for password or passwd on your computer’s drives. You may be shocked to find what’s on your systems. Some programs even write passwords to disk or leave them stored in memory.
Weak password storage is a criminal hacker’s dream. Head it off if you can. This doesn’t mean that you should immediately run off and start using a cloud-based password manager, however. As we’ve all seen over the years, those systems get hacked as well!
Countermeasures against weak passwords
The only reliable way to eliminate weak password storage is to use only applications that store passwords securely. This practice may not be practical, but it’s your only guarantee that your passwords are secure. Another option is to instruct users not to store their passwords when prompted.
Before upgrading applications, contact your software vendor to see how it manages passwords, or search for a third-party solution.
How hackers use network analyzers to crack passwords
A network analyzer sniffs the packets traversing the network, which is what the bad guys do if they can gain control of a computer, tap into your wireless network, or gain physical network access to set up their network analyzer. If they gain physical access, they can look for a network jack on the wall and plug right in.
Delta Plc Password Crack Tool
Finding password vulnerabilities with network analyzers
Gmail Password Crack Tool
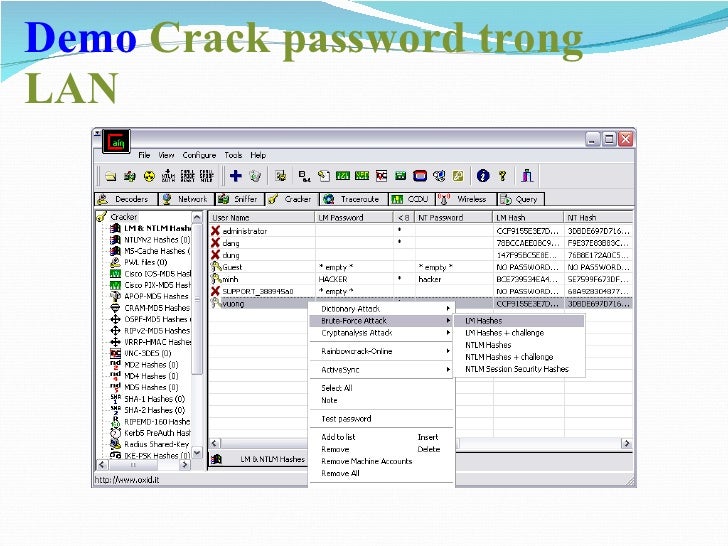
The image below shows how crystal-clear passwords can be through the eyes of a network analyzer. This shows how Cain & Abel can glean thousands of passwords going across the network in a matter of a couple of hours. As you can see in the left pane, these clear text password vulnerabilities can apply to FTP, web, Telnet, and more. (The actual usernames and passwords are blurred to protect them.)
If traffic isn’t tunneled through some form of encrypted link (such as a virtual private network, Secure Shell, or Secure Sockets Layer), it’s vulnerable to attack.
Excel Password Crack Tool Download
Cain & Abel is a password-cracking tool that also has network analysis capabilities. You can also use a regular network analyzer, such as the commercial products Omnipeek and CommView, as well as the free open-source program Wireshark. With a network analyzer, you can search for password traffic in various ways. To capture POP3 password traffic, for example, you can set up a filter and a trigger to search for the PASS command. When the network analyzer sees the PASS command in the packet, it captures that specific data.
Network analyzers require you to capture data on a hub segment of your network or via a monitor/mirror/span port on a switch. Otherwise, you can’t see anyone else’s data traversing the network — just yours. Check your switch’s user guide to see whether it has a monitor or mirror port and for instructions on how to configure it. You can connect your network analyzer to a hub on the public side of your firewall. You’ll capture only those packets that are entering or leaving your network — not internal traffic.
Countermeasures against network analyzers
Here are some good defenses against network analyzer attacks:
- Use switches on your network, not hubs. Ethernet hubs are things of the past, but they are still used occasionally. If you must use hubs on network segments, a program like sniffdet for Unix/Linux-based systems and PromiscDetect for Windows can detect network cards in promiscuous mode (accepting all packets, whether they’re destined for the local machine or not). A network card in promiscuous mode signifies that a network analyzer may be running on the network.
- Make sure that unsupervised areas, such as an unoccupied lobby or training room, don’t have live network connections. An Ethernet port is all someone needs to gain access to your internal network.
- Don’t let anyone without a business need gain physical access to your switches or to the network connection on the public side of your firewall. With physical access, a hacker can connect to a switch monitor port or tap into the unswitched network segment outside the firewall and then capture packets.
Switches don’t provide complete security because they’re vulnerable to ARP poisoning attacks.
How hackers break weak BIOS passwords
Most computer BIOS (basic input/output system) settings allow power-on passwords and/or setup passwords to protect the computer’s hardware settings that are stored in the CMOS chip. Here are some ways around these passwords:
- You usually can reset these passwords by unplugging the CMOS battery or by changing a jumper on the motherboard.
- Password-cracking utilities for BIOS passwords are available on the Internet and from computer manufacturers.
If gaining access to the hard drive is your ultimate goal, you can remove the hard drive from the computer and install it in another one, and you’re good to go. This technique is a great way to prove that BIOS/power-on passwords are not effective countermeasures for lost or stolen laptops.
Check cirt.net for a good list of default system passwords for various vendor equipment.
Tons of variables exist for hacking and hacking countermeasures depending on your hardware setup. If you plan to hack your own BIOS passwords, check for information in your user manual, or refer to the BIOS password-hacking guide. If protecting the information on your hard drives is your ultimate goal, full (sometimes referred to as whole) disk is the best way to go. The good news is that newer computers (within the past five years or so) use a new type of BIOS called unified extensible firmware interface (UEFI), which is much more resilient to boot-level system cracking attempts. Still, a weak password may be all it takes for the system to be exploited.
Weak passwords in limbo
Bad guys often exploit user accounts that have just been created or reset by a network administrator or help desk. New accounts may need to be created for new employees or even for security testing purposes. Accounts may need to be reset if users forget their passwords or if the accounts have been locked out because of failed attempts.
Password weaknesses in user account
Here are some reasons why user accounts can be vulnerable:
- When user accounts are reset, they’re often assigned an easily cracked or widely-known password (such as the user’s name or the word password). The time between resetting the user account and changing the password is a prime opportunity for a break-in.
- Many systems have default accounts or unused accounts with weak passwords or no passwords at all. These accounts are prime targets.
Countermeasures against passwords in limbo
The best defenses against attacks on passwords in limbo are solid help-desk policies and procedures that prevent weak passwords from being available at any given time during the new-account-generation and password-reset processes. Following are perhaps the best ways to overcome this vulnerability:
Require users to be on the phone with the help desk or to have a help-desk member perform the reset at the user’s desk.
Require that the user immediately log in and change the password.
If you need the ultimate in security, implement stronger authentication methods, such as challenge/response questions, smart cards, or digital certificates.
Automate password reset functionality via self-service tools on your network so that users can manage most of their password problems without help from others.
